 adware- spam; is any program that automatically displays or offers unwanted advertising, whether embedded in a web page through graphics, posters, floating windows, or during the installation of a program to the user, in order to generate profit to their authors.
adware- spam; is any program that automatically displays or offers unwanted advertising, whether embedded in a web page through graphics, posters, floating windows, or during the installation of a program to the user, in order to generate profit to their authors. 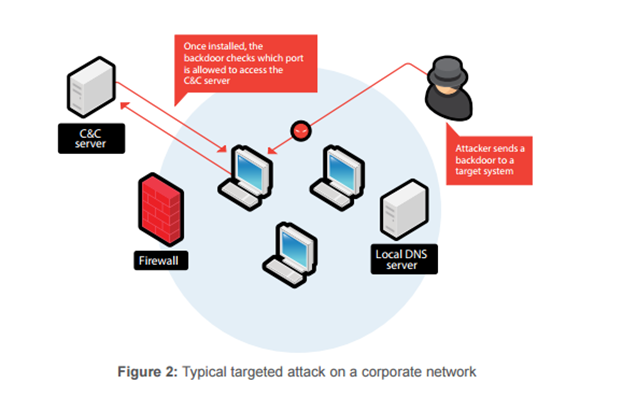
back door; is a special sequence within the programming code, by means of which algorithm security
 Cookies; is a small information sent by a website and stored in the user's browser, so that the website can consult the previous activity of the browser.
Cookies; is a small information sent by a website and stored in the user's browser, so that the website can consult the previous activity of the browser.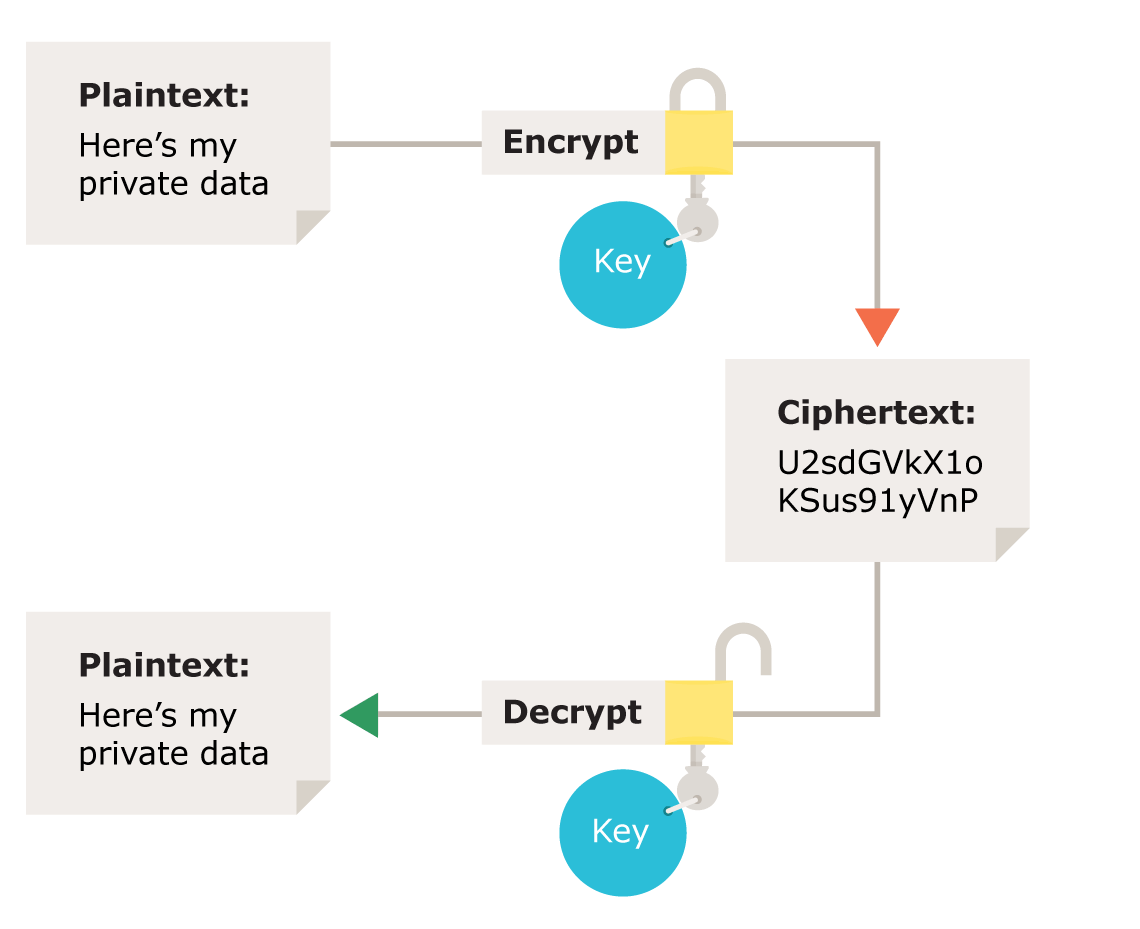
encrynption; is the process of encoding a message or information in such a way that only authorized parties can access it and those who are not authorized cannot. Encryption does not itself prevent interference, but denies the intelligible content to a would-be interceptor.
 hacker; is any individual who is dedicated to enthusiastic programming, that is, an enthusiastic expert of any kind.
hacker; is any individual who is dedicated to enthusiastic programming, that is, an enthusiastic expert of any kind. malware; The term is used to talk about all kinds of computer threats or hostile software, and there are different types of malware depending on their origin and consequences. Among them we find viruses, worms, trojans, keyloggers, botnets, spyware, adware, ransomware and sacareware.
malware; The term is used to talk about all kinds of computer threats or hostile software, and there are different types of malware depending on their origin and consequences. Among them we find viruses, worms, trojans, keyloggers, botnets, spyware, adware, ransomware and sacareware. phishing; it is committed through the use of a type of social engineering, characterized by trying to acquire confidential information in a fraudulent way (such as a password, detailed information about credit cards or other banking information).
phishing; it is committed through the use of a type of social engineering, characterized by trying to acquire confidential information in a fraudulent way (such as a password, detailed information about credit cards or other banking information).spyware; or spyware is a malware that collects information from a computer and then transmits this information to an external entity without the knowledge or consent of the computer owner.
 virus; for the purpose of altering the normal operation of any type of computing device, without the permission or knowledge of the user mainly to achieve malicious purposes on the device. Viruses, usually, replace executable files by others infected with the code of this. Viruses can destroy, intentionally, the data stored in a computer, although there are also other more harmless, which only cause discomfort or unforeseen.
virus; for the purpose of altering the normal operation of any type of computing device, without the permission or knowledge of the user mainly to achieve malicious purposes on the device. Viruses, usually, replace executable files by others infected with the code of this. Viruses can destroy, intentionally, the data stored in a computer, although there are also other more harmless, which only cause discomfort or unforeseen.
Comentarios
Publicar un comentario